In this section you will set up the authentication method and parameters for your LDAP directory. There are two bind types and two authentication methods you can use.
Bind Types
Bind operations are used to authenticate clients to the directory server, establish an authorization identity that will be used for subsequent operations processed on that connection, and to specify the LDAP protocol version that the client will use.
There are two bind types available to you:
- Anonymous Bind - Uses a simple bind or a search bind. Anyone can connect to the LDAP server. This bind type does not require a Lookup DN or Lookup Password.
- LDAP Credentials - Requires a Lookup DN and Lookup Password. LDAP credentials must be previously established.
Authentication methods
There are two authentication methods available to you.
-
Simple bind. Authentication by simple bind is the most common way to authenticate an LDAP client, but you can also choose a search bind authentication method. You can either bind Anonymously, or you can provide LDAP credentials such as a lookup DN and lookup password. In either case, you must provide a user DN template. Choose Simple bind if your LDAP user name is part of your distinguished name (DN).
-
Search bind. While the simple bind connection takes place in a single step, the search/bind operation requires two steps. First the directory is searched for the user name attribute. If located, a bind operation ensues to check the user’s credentials against the external directory. You must specify a user search base and a user search filter template. In some methods, you must also specify a lookup DN and lookup password. Choose Search bind if you have an LDAP user name that is not a part of the distinguished name (DN).
Anonymous Bind with Simple Bind
When you choose Anonymous Bind with Simple Bind, you must provide a User DN Template.
-
In the Add Directory window, click Authentication.
-
Under Bind Type, click on Anonymous Bind.
-
Under Authentication Method, click on Simple Bind.
-
Enter a DN template that the external LDAP directory can use to locate user accounts in the User DN Template field. This string must include
%(username)s, which DC/OS will replace with the user name provided by the user at login. Some examples are:cn=%(username)s,dc=los-pollos,dc=io uid=%(username)s,cn=users,cn=accounts,dc=demo1,dc=freeipa,dc=org uid=%(username)s,ou=users,dc=example,dc=com -
When you have completed your entries, the dialog should look like the following.
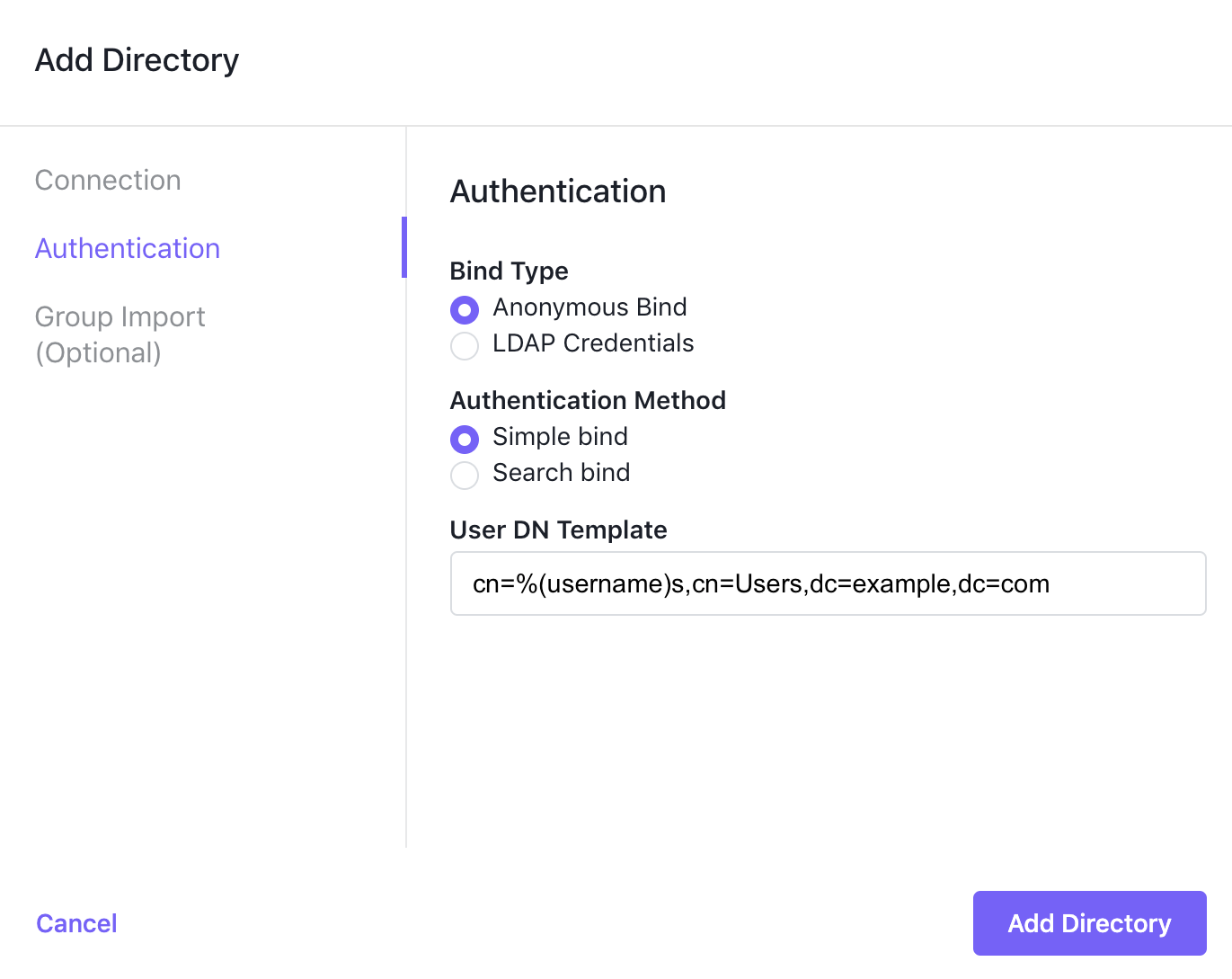
Figure 1. Anonymous Bind with Simple Bind parameters
-
Click Add Directory.
Anonymous Bind with Search Bind
When you choose Anonymous Bind with Search Bind, you must provide a User Search Base and a User Search Filter Template.
-
In the Add Directory window, click Authentication.
-
Under Bind Type, click on Anonymous Bind.
-
Under Authentication Method, click on Search Bind.
-
In the User Search Base field, specify where in the directory to begin the search for the LDAP user name. This should be the DN of the search base object. An example would be:
cn=Users,dc=example,dc=com -
Specify the template for translating the LDAP user name to a valid LDAP search filter in the User Search Filter Template field. This entry must contain the following placeholder:
%(username)s. Some examples would be:(sAMAccountName=%(username)s) (uid=%(username)s) -
When you have completed your entries, the dialog should look like the following:
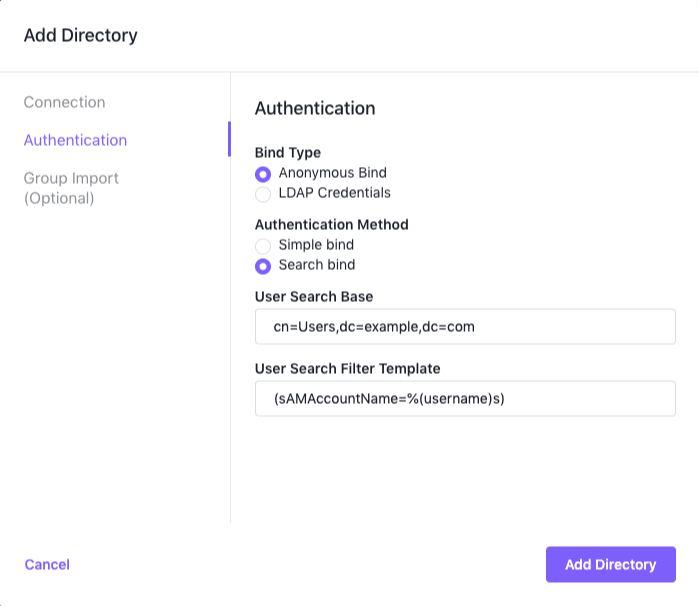
Figure 2. Anonymous Bind with Search Bind parameters
-
Click Add Directory.
LDAP Credentials with Simple Bind
When you choose LDAP Credentials as your bind type, and Simple Bind as your Authentication type, you must supply the Lookup DN, Lookup Password, and User DN Template.
-
In the Add Directory window, click Authentication.
-
Under Bind Type, click on LDAP Credentials.
-
Under Authentication Method, click Simple bind.
-
Provide the full DN of the user account you will use to connect to the LDAP server to import users, groups, and check user credentials in the Lookup DN field. A few examples are:
cn=read-only-user,dc=los-pollos,dc=io uid=read-only-user,cn=users,cn=accounts,dc=demo1,dc=freeipa,dc=org uid=read-only-user,ou=users,dc=example,dc=com -
Provide the password of the account in the Lookup Password field.
-
Enter a DN template that the external LDAP directory can use to locate user accounts in the User DN Template field. This string must include
%(username)s, which DC/OS will replace with the user name provided by the user at login. Some examples are:cn=%(username)s,dc=los-pollos,dc=io uid=%(username)s,cn=users,cn=accounts,dc=demo1,dc=freeipa,dc=org uid=%(username)s,ou=users,dc=example,dc=com -
When you have completed your entries, the dialog should look like the following.
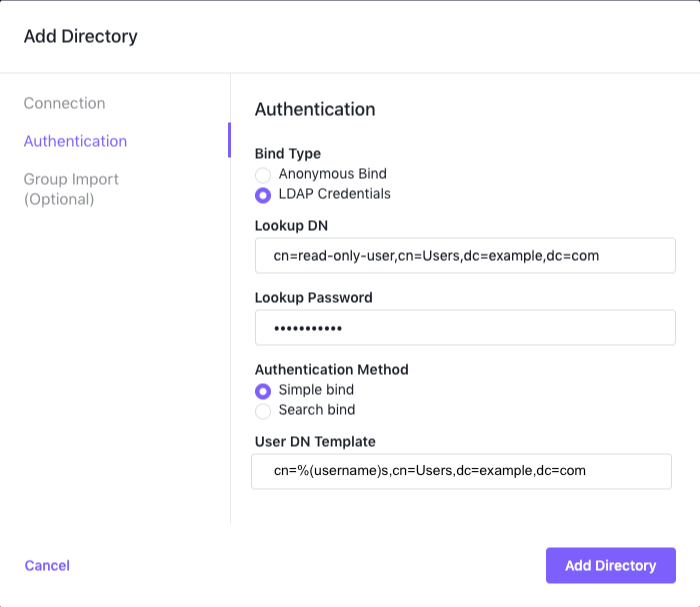
Figure 3. LDAP Credentials with Simple Bind parameters
-
Click Add Directory.
LDAP Credentials with Search Bind
When you choose LDAP Credentials as your bind type, and Search Bind as your Authentication type, you must supply the Lookup DN, Lookup Password, User Search Base and User Search Filter Template.
-
In the Add Directory window, click Authentication.
-
Under Bind Type, click on LDAP Credentials.
-
Provide the full DN of the user account you will use to connect to the LDAP server to import users, groups, and check user credentials in the Lookup DN field. A few examples are:
cn=read-only-user,dc=los-pollos,dc=io uid=read-only-user,cn=users,cn=accounts,dc=demo1,dc=freeipa,dc=org uid=read-only-user,ou=users,dc=example,dc=com -
Provide the password of the account in the Lookup Password field.
-
Under Authentication Method, click Search bind.
-
In the User Search Base field, specify where in the directory to begin the search for the LDAP user name. This should be the DN of the search base object. An example would be:
cn=Users,dc=example,dc=com -
Specify the template for translating the LDAP user name to a valid LDAP search filter in the User Search Filter Template field. This entry must contain the following placeholder:
%(username)s. Some examples would be:(sAMAccountName=%(username)s) (uid=%(username)s) -
When you have completed your entries, the dialog should look like the following:
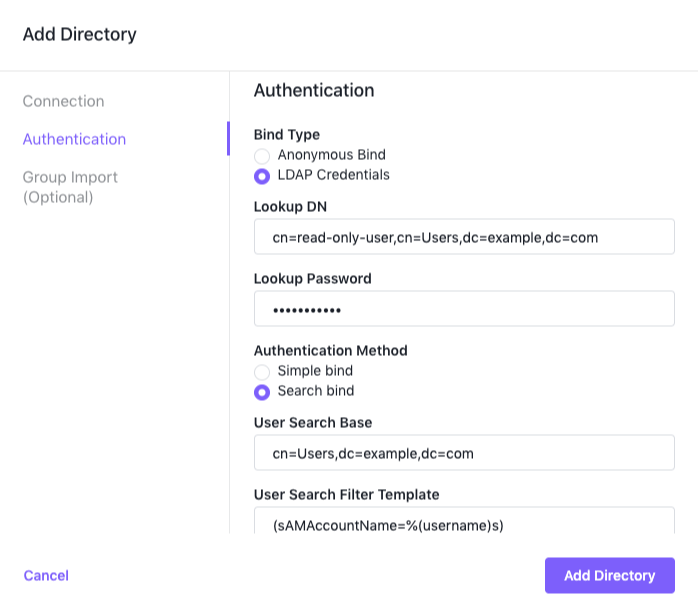
Figure 4. LDAP Credentials with Search Bind parameters
-
Click Add Directory.
 DC/OS Documentation
DC/OS Documentation