You can implement fine-grained user access to services using either the DC/OS web interface or the API, or the CLI.
The Marathon permissions allow you to restrict a user’s access to services on either a per service or a per service group basis. This section walks you through the steps to accomplish this.
Marathon permissions and Mesos permissions do not distinguish between service names, job names, service groups, or job groups. Therefore your naming must be unique.
Prerequisites:
- You must have the DC/OS CLI installed and be logged in as a superuser.
- A user account to assign permissions to.
Granting access to a service
Using the DC/OS web interface
-
Log into the DC/OS web interface as a user with the
superuserpermission.
Figure 1. DC/OS web interface login screen
-
Select Organization and choose Users or Groups.
-
Select the name of the user or group to grant the permission to.
Figure 2. Select user to grant permissions
-
From the Permissions tab, click ADD PERMISSION.
-
Click INSERT PERMISSION STRING to toggle the dialog.
-
Copy and paste the permission in the Permissions Strings field. Choose the permission strings based on your security mode.
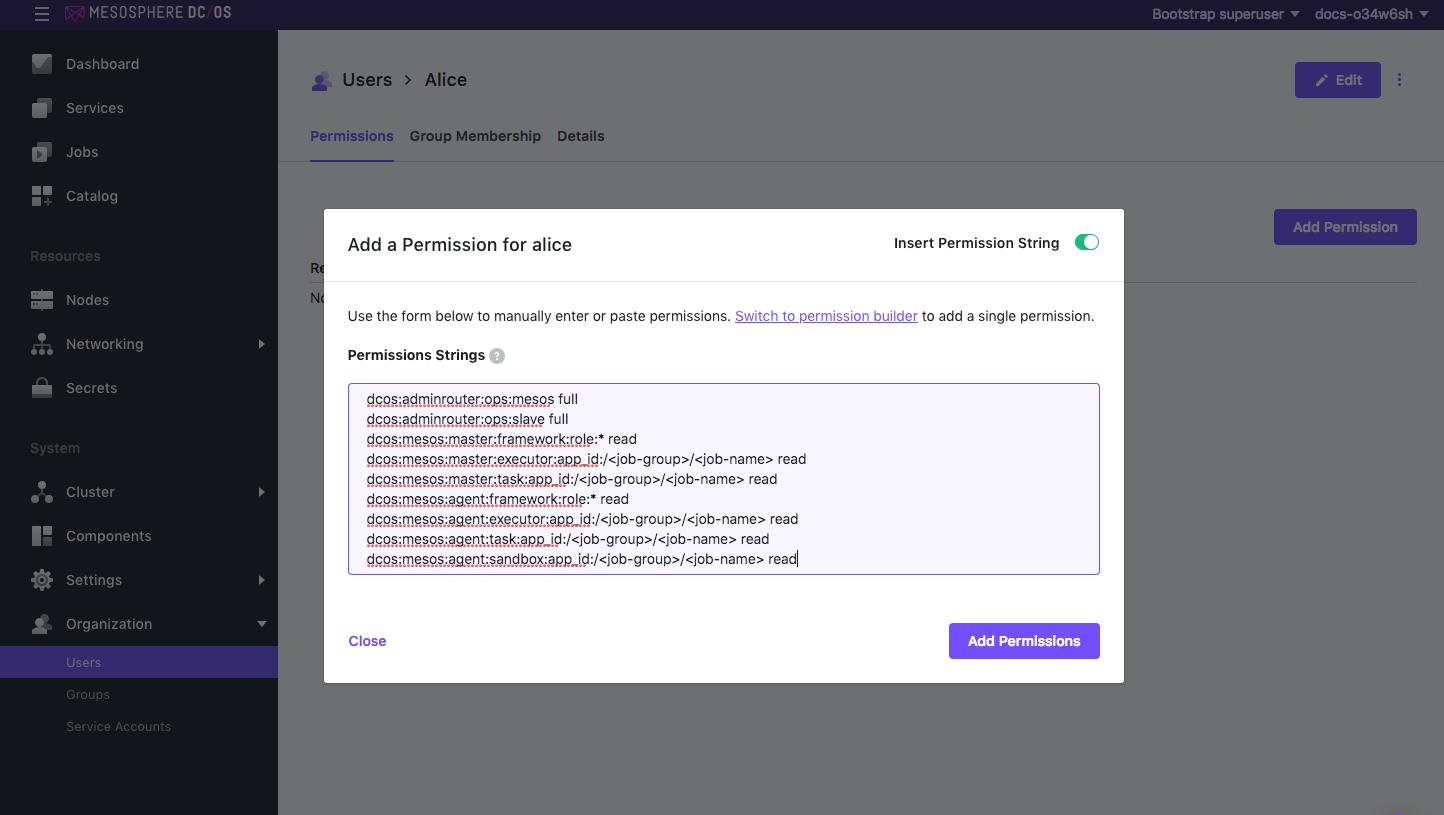
Figure 3. Copy and paste permissions string.
Permissive
-
DC/OS service access:
Specify your service (
<service-name>) and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:marathon:marathon:services:/<service-name> read,update.dcos:adminrouter:service:marathon full dcos:service:marathon:marathon:services:/<service-name> <action> -
DC/OS service tasks and logs:
dcos:adminrouter:ops:slave full
Strict
-
DC/OS service access:
Specify your service (
<service-name>) and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:marathon:marathon:services:/<service-name> read,update.dcos:adminrouter:service:marathon full dcos:service:marathon:marathon:services:/<service-name> <action> -
DC/OS service tasks and logs:
dcos:adminrouter:ops:slave full dcos:mesos:agent:executor:app_id:/<service-name> read dcos:mesos:agent:framework:role:slave_public read dcos:mesos:agent:sandbox:app_id:/<service-name> read dcos:mesos:agent:task:app_id:/<service-name> read dcos:mesos:master:executor:app_id:/<service-name> read dcos:mesos:master:framework:role:slave_public read dcos:mesos:master:task:app_id:/<service-name> read
-
-
Click ADD PERMISSIONS and then Close.
Via the CLI
Prerequisites:
-
You must have the DC/OS CLI installed and be logged in as a superuser.
-
To grant permissions to a group instead of a user, replace
users grant <uid>withgroups grant <gid>.
Permissive
-
DC/OS service access:
-
Grant the following privileges to the user
uidfor a particular service (<service-name>).dcos security org users grant <uid> dcos:adminrouter:service:marathon full dcos security org users grant <uid> dcos:service:marathon:marathon:services:/<service-name> full --description "Controls access to a service or service group <service-name>"
-
-
DC/OS service tasks and logs:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:ops:mesos full dcos security org users grant <uid> dcos:adminrouter:ops:slave full
-
Strict
-
DC/OS service access:
-
Grant the following privileges to the user
uidfor a particular service (<service-name>).dcos security org users grant <uid> dcos:adminrouter:service:marathon full dcos security org users grant <uid> dcos:service:marathon:marathon:services:/<service-name> full --description "Controls access to a service or service group <service-name>"
-
-
DC/OS service tasks and logs:
-
Grant the following privileges to the user
uidfor a particular service (<service-name>).dcos security org users grant <uid> dcos:adminrouter:ops:mesos full dcos security org users grant <uid> dcos:adminrouter:ops:slave full dcos security org users grant <uid> dcos:mesos:agent:executor:app_id:/<service-name> read --description "Controls access to executors of a service, job, service group, or job group named <service-name>" dcos security org users grant <uid> dcos:mesos:agent:framework:role:slave_public read --description "Controls access to information about frameworks registered under the slave_public role" dcos security org users grant <uid> dcos:mesos:agent:sandbox:app_id:/<service-name> read --description "Controls access to the sandbox data of a service, job, service group, or job group named <service-name>" dcos security org users grant <uid> dcos:mesos:agent:task:app_id:/<service-name> read --description "Controls access to tasks of a service, job, service group, or job group named <service-name>" dcos security org users grant <uid> dcos:mesos:master:executor:app_id:/<service-name> read --description "Controls access to executors running inside a service, job, service group, or job group named <service-name>" dcos security org users grant <uid> dcos:mesos:master:framework:role:slave_public read --description "Controls access to frameworks registered with the slave_public role" dcos security org users grant <uid> dcos:mesos:master:task:app_id:/<service-name> read --description "Controls access to tasks of a service, job, service group, or job group named <service-name>"
-
Granting access to a service in a service group
Via the DC/OS web interface
-
Log into the DC/OS web interface as a user with the
superuserpermission.
Figure 3. DC/OS web interface login screen
-
Select Organization and choose Users or Groups.
-
Select the name of the user or group to grant the permission to.

Figure 4. Select user to grant permissions
-
From the Permissions tab, click ADD PERMISSION.
-
Click INSERT PERMISSION STRING to toggle the dialog.

Figure 5. Add permission
-
Copy and paste the permission in the Permissions Strings field. Choose the permission strings based on your security mode.
Permissive
-
DC/OS service access:
Specify your service (
<service-name>), group (<gid>), and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:marathon:marathon:services:/<service-name> read,update.dcos:adminrouter:service:marathon full dcos:service:marathon:marathon:services:/<gid>/<service-name> <action> -
DC/OS service tasks and logs:
dcos:adminrouter:ops:mesos full dcos:adminrouter:ops:slave full
Strict
-
DC/OS service access:
Specify your service (
<service-name>), group (<gid>), and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:marathon:marathon:services:/<service-name> read,update.dcos:adminrouter:service:marathon full dcos:service:marathon:marathon:services:/<gid>/<service-name> <action> -
DC/OS service tasks and logs:
dcos:adminrouter:ops:mesos full dcos:adminrouter:ops:slave full dcos:mesos:agent:executor:app_id:/<gid>/<service-name> read dcos:mesos:agent:framework:role:slave_public read dcos:mesos:agent:sandbox:app_id:/<gid>/<service-name> read dcos:mesos:agent:task:app_id:/<gid>/<service-name> read dcos:mesos:master:executor:app_id:/<gid>/<service-name> read dcos:mesos:master:framework:role:slave_public read dcos:mesos:master:task:app_id:/<gid>/<service-name> read
-
-
Click ADD PERMISSIONS and then Close.
Via the CLI
Prerequisites:
- You must have the DC/OS CLI installed and be logged in as a superuser.
Tips:
- To grant permissions to a group instead of a user, replace
users grant <uid>withgroups grant <gid>.
Permissive
-
DC/OS service access:
-
Grant the following privileges to the user
uidfor a particular service (<service-name>).dcos security org users grant <uid> dcos:adminrouter:service:marathon full dcos security org users grant <uid> dcos:service:marathon:marathon:services:/group/<service-name> full --description "Controls access to a service or service group <service-name> inside a group called group"
-
-
DC/OS service tasks and logs:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:ops:mesos full dcos security org users grant <uid> dcos:adminrouter:ops:slave full
-
Strict
-
DC/OS service access:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:service:marathon full dcos security org users grant <uid> dcos:service:marathon:marathon:services:/group/<service-name> full --description "Controls access to a service or service group <service-name> inside a group called group"
-
-
DC/OS service tasks and logs:
-
Grant the following privileges to the user
uidfor a particular service (<service-name>).dcos security org users grant <uid> dcos:adminrouter:ops:mesos full dcos security org users grant <uid> dcos:adminrouter:ops:slave full dcos security org users grant <uid> dcos:mesos:agent:executor:app_id:/group/<service-name> read --description "Controls access to executors of a service, job, service group, or job group named <service-name> inside the group group" dcos security org users grant <uid> dcos:mesos:agent:framework:role:slave_public read --description "Controls access to information about frameworks registered under the slave_public role" dcos security org users grant <uid> dcos:mesos:agent:sandbox:app_id:/group/<service-name> read --description "Controls access to the sandbox data of a service, job, service group, or job group named <service-name> inside the group group" dcos security org users grant <uid> dcos:mesos:agent:task:app_id:/group/<service-name> read --description "Controls access to tasks of a service, job, service group, or job group named <service-name> inside the group group" dcos security org users grant <uid> dcos:mesos:master:executor:app_id:/group/<service-name> read --description "Controls access to executors running inside a service, job, service group, or job group named <service-name>" dcos security org users grant <uid> dcos:mesos:master:framework:role:slave_public read --description "Controls access to frameworks registered with the slave_public role" dcos security org users grant <uid> dcos:mesos:master:task:app_id:/group/<service-name> read --description "Controls access to tasks of a service, job, service group, or job group named <service-name>"
-
Granting a user access to a service group
Via the DC/OS web interface
-
Log into the DC/OS web interface as a user with the
superuserpermission.
Figure 5. DC/OS web interface login screen
-
Select Organization and choose Users or Groups.
-
Select the name of the user or group to grant the permission to.

Figure 6. Select user to grant permissions
-
From the Permissions tab, click ADD PERMISSION.
-
Click INSERT PERMISSION STRING to toggle the dialog.

Figure 7. Add permissions
-
Copy and paste the permission in the Permissions Strings field. Choose the permission strings based on your security mode.
Permissive
-
DC/OS group access:
Specify your group (
<gid>) and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:marathon:marathon:services:/<service-name> read,update.dcos:adminrouter:service:marathon full dcos:service:marathon:marathon:services:/<gid> <action> -
Group tasks and logs:
dcos:adminrouter:ops:mesos full dcos:adminrouter:ops:slave full
Strict
-
DC/OS group access:
Specify your group (
<gid>) and action (<action>). Actions can be eithercreate,read,update,delete, orfull. To permit more than one operation, use a comma to separate them, for example:dcos:service:marathon:marathon:services:/<service-name> read,update.dcos:adminrouter:service:marathon full dcos:service:marathon:marathon:services:/<gid> <action> -
Group tasks and logs:
dcos:adminrouter:ops:mesos full dcos:adminrouter:ops:slave full dcos:mesos:agent:executor:app_id:/<gid> read dcos:mesos:agent:framework:role:slave_public read dcos:mesos:agent:sandbox:app_id:/<gid> read dcos:mesos:agent:task:app_id:/<gid> read dcos:mesos:master:executor:app_id:/<gid> read dcos:mesos:master:framework:role:slave_public read dcos:mesos:master:task:app_id:/<gid> read
-
-
Click ADD PERMISSIONS and then Close.
Via the CLI
Prerequisites:
- You must have the DC/OS CLI installed and be logged in as a superuser.
Tips:
- To grant permissions to a group instead of a user, replace
users grant <uid>withgroups grant <gid>.
Permissive
-
DC/OS group access:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:service:marathon full dcos security org users grant <uid> dcos:service:marathon:marathon:services:/group full --description "Controls access to a service, job, service group, or job group named group"
-
-
Group tasks and logs:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:ops:mesos full dcos security org users grant <uid> dcos:adminrouter:ops:slave full
-
Strict
-
DC/OS group access:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:service:marathon full dcos security org users grant <uid> dcos:service:marathon:marathon:services:/group full --description "Controls access to a service, job, service group, or job group named group"
-
-
Group tasks and logs:
-
Grant the following privileges to the user
uid.dcos security org users grant <uid> dcos:adminrouter:ops:mesos full dcos security org users grant <uid> dcos:adminrouter:ops:slave full dcos security org users grant <uid> dcos:mesos:agent:executor:app_id:/group read --description "Controls access to executors of a service, job, service group, or job group named group" dcos security org users grant <uid> dcos:mesos:agent:framework:role:slave_public read --description "Controls access to information about frameworks registered under the slave_public role" dcos security org users grant <uid> dcos:mesos:agent:sandbox:app_id:/group read --description "Controls access to the sandbox data of a service, job, service group, or job group named group" dcos security org users grant <uid> dcos:mesos:agent:task:app_id:/group read --description "Controls access to tasks of a service, job, service group, or job group named group" dcos security org users grant <uid> dcos:mesos:master:executor:app_id:/group read --description "Controls access to executors running inside a service, job, service group, or job group named group" dcos security org users grant <uid> dcos:mesos:master:framework:role:slave_public read --description "Controls access to frameworks registered with the slave_public role" dcos security org users grant <uid> dcos:mesos:master:task:app_id:/group read --description "Controls access to tasks of a service, job, service group, or job group named group"
-
 DC/OS Documentation
DC/OS Documentation