After you have configured a directory service or an identity provider, you can add the users to DC/OS so that you can assign permissions.
Prerequisites
- An external LDAP directory.
- An OpenID Connect or SAML provider.
Adding external users via logon attempt
By default, users have no DC/OS permissions. Any attempts to access DC/OS without permissions will fail. However, if you have successfully configured an LDAP directory or an identity provider and the user provides valid credentials, the logon attempt will cause the user’s account to be added to DC/OS.
Requirement: The user’s name and password must be correct.
Because you will need the user account in DC/OS before you can add any permissions, you may find it easiest to ask each of the users to try to log on to DC/OS. Though their attempts will fail, this will serve to populate DC/OS with their accounts.
Importing external LDAP users individually from the web interface
Use the following instructions to import an external user:
-
Select Organization > Users and create a new user.
-
Select Import LDAP User.
-
Type the user’s user name or ID in the User Name box.
-
Click Add.
-
When you have finished adding all of your users, click the Close button.
Importing groups of LDAP users
About importing LDAP groups
You can import existing LDAP user groups into DC/OS. Starting in DC/OS Enterprise 1.12, imported LDAP groups are supported by LDAP sync. DC/OS periodically synchronizes the external LDAP directory, by default this is set to every 1800 seconds (30 mins).
Requirement: Group entries in the LDAP directory must list their members with the member, uniquemember, or memberuid attribute.
Group size is limited to 100 users. To increase this limit, contact Mesosphere customer support. If the user name matches an existing user, it is not reimported. You can check the logs to determine if this has occurred.
Configuring LDAP group import
Use the following instructions to configure LDAP group import:
-
Open the Settings -> LDAP Directories tab.
-
Click ADD DIRECTORY.
-
Click Group Import (Optional).
-
Provide the DN for the subset of the directory tree that should be searched in the GROUP SEARCH BASE field. Example:
(cn=Users,dc=mesosphere,dc=com). -
Provide a template to be used to translate a group name to a valid LDAP search filter in the GROUP SEARCH FILTER TEMPLATE field. The string must contain
%(groupname). Example:(&(objectclass=group)(sAMAccountName=%(groupname)s)). -
When completed, the LDAP group import configuration dialog appears as shown in Figure 1.
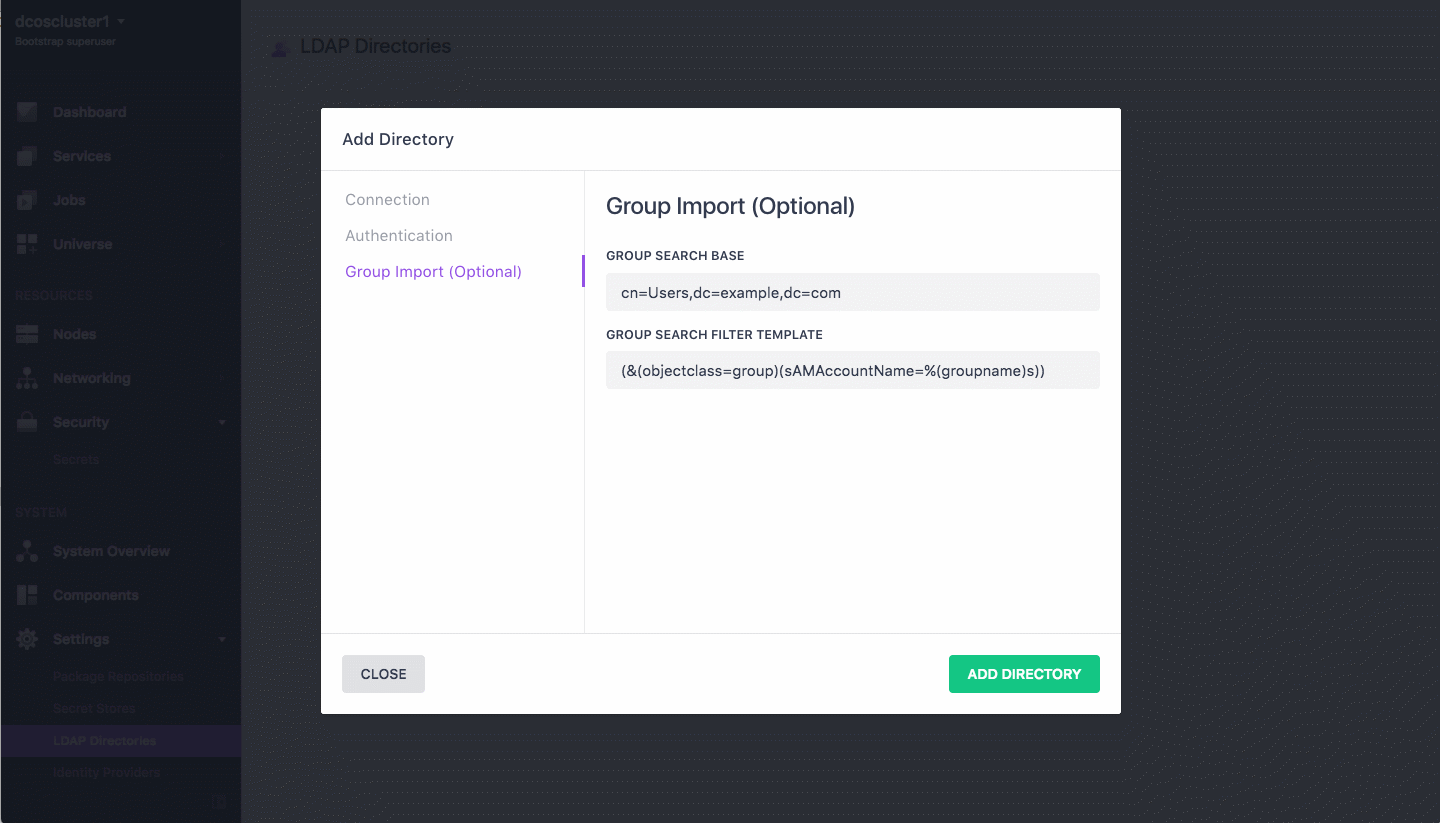
Figure 1. LDAP group import configuration
-
Click ADD DIRECTORY.
Importing LDAP groups using the web interface
-
In the Organization -> Groups tab, click the + icon in the top right and select Import LDAP Group.
-
Type the LDAP group name in the Name box. The group name must not match the name of an existing group.
-
Click Add Group. This creates a user group in DC/OS with the same name as the LDAP group and imports all of the users in the LDAP group into DC/OS.
-
When you have finished adding all of your groups, click the Close button.
Importing LDAP groups using the API
You can import a group of LDAP users by using the /ldap/importuser IAM API endpoint.
Prerequisites:
- The
group-searchconfiguration key must be set, as discussed in Configuring LDAP group import. - The existing group entries must list their members by using the
member,uniquemember, ormemberuidattribute. - You must follow the steps in Obtaining the root certificate of your DC/OS CA before issuing the curl commands in this section.
In this example, a group named johngroup is imported.
-
Log in to the CLI to ensure that you can reference the cluster URL as shown in the following code samples.
-
Initiate import using the following command.
curl -i -X POST --cacert dcos-ca.crt -H "Authorization: token=$(dcos config show core.dcos_acs_token)" --data '{"groupname": "johngroup"}' --header "Content-Type: application/json" $(dcos config show core.dcos_url)/acs/api/v1/ldap/importgroup -
Confirm that
johngroupis added.curl --cacert dcos-ca.crt -H "Authorization: token=$(dcos config show core.dcos_acs_token)" $(dcos config show core.dcos_url)/acs/api/v1/groups/johngroupcurl --cacert dcos-ca.crt -H "Authorization: token=$(dcos config show core.dcos_acs_token)" $(dcos config show core.dcos_url)/acs/api/v1/groups/johngroup/users
 DC/OS Documentation
DC/OS Documentation