You can grant users access to the Components tab. By default, new users have no permissions.
Grant Access by using the UI
Prerequisites:
- A DC/OS user account without the
dcos:superuserpermission.
-
Log in to the DC/OS UI as a user with the
superuserpermission.
Figure 1. Log in to the UI
-
Select Organization and choose Users or Groups.
-
Select the name of the user or group to grant the permission to.
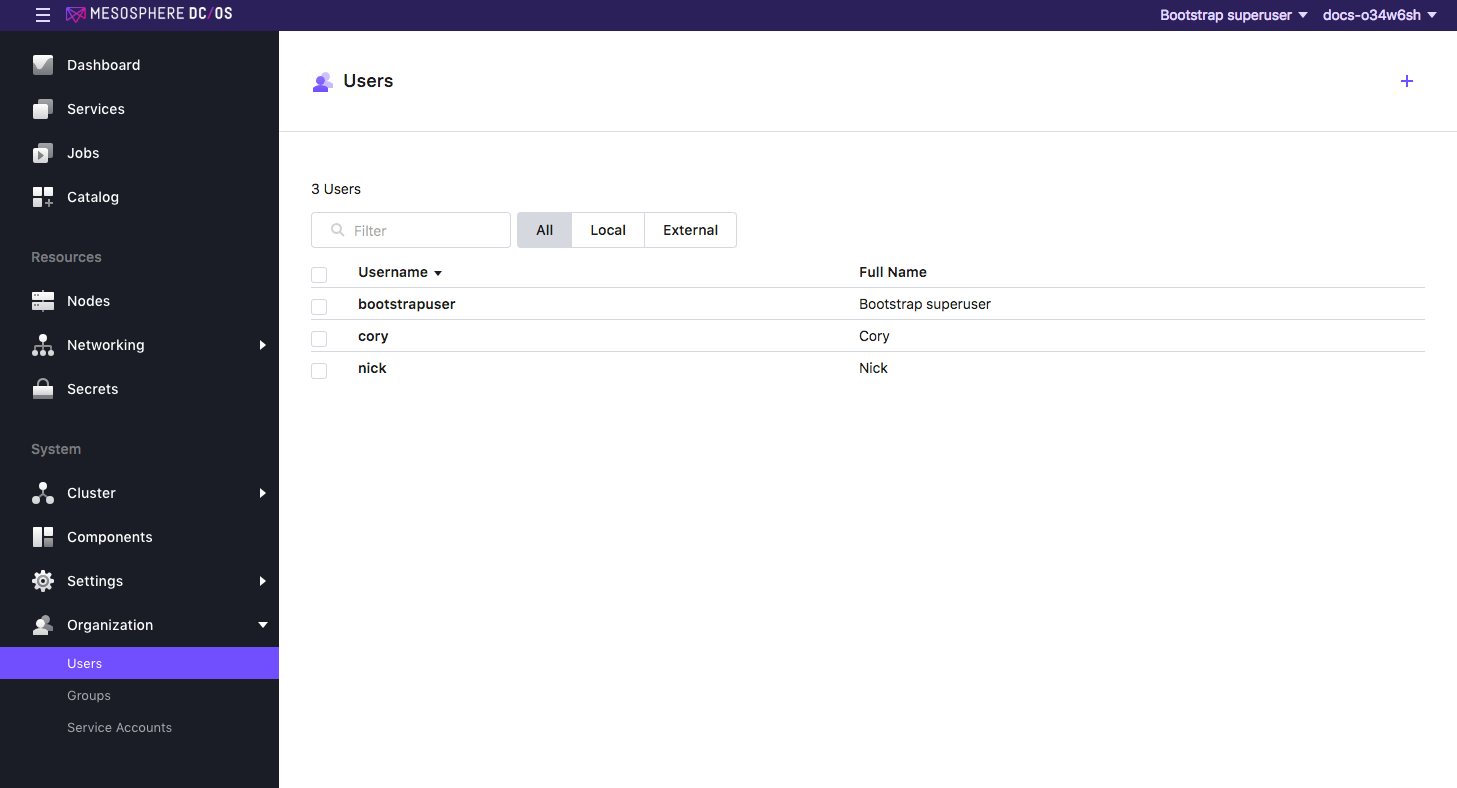
Figure 2. Select user or group to grant permissions to
-
From the Permissions screen, click ADD PERMISSION.
-
Click INSERT PERMISSION STRING to toggle the dialog.
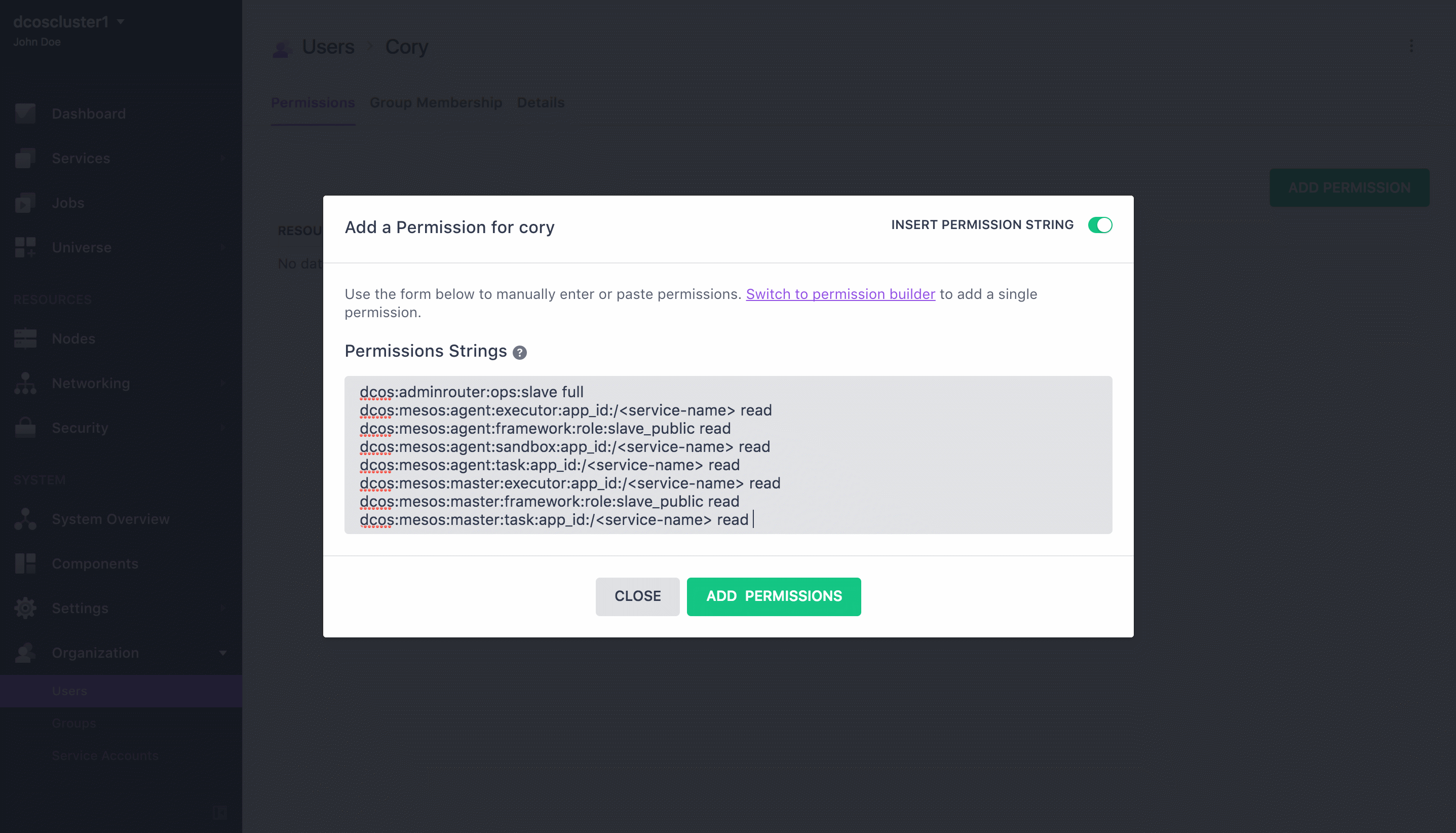
Figure 3. Add permission
-
Copy and paste the permission in the Permissions Strings field. Choose the permission strings based on your security mode and click ADD PERMISSIONS and then Close.
Permissive
Components Tab
dcos:adminrouter:ops:historyservice full dcos:adminrouter:ops:system-health fullStrict
Components Tab
dcos:adminrouter:ops:historyservice full dcos:adminrouter:ops:system-health full
Granting Access by using the API
Prerequisites:
- You must have the DC/OS CLI installed and be logged in as a superuser.
- You must get the root cert before issuing the
curlcommands in this section.
Notes
- Service resources often include
/characters that must be replaced with%252Fincurlrequests, as shown in the examples below. - When using the API to manage permissions, you must create the permission before granting it. If the permission already exists, the API will return an informative message and you can continue to assign the permission.
Permissive
-
Create the permission.
curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" \ -H 'Content-Type: application/json' \ $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:historyservice \ -d '{"description":"Grants access to the contents of the Components screen"}' curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" \ -H 'Content-Type: application/json' \ $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:system-health \ -d '{"description":"Grants access to the Components screen"}' -
Grant the following privileges to the user
uid.curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:historyservice/users/<uid>/full curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:system-health/users/<uid>/full
Strict
-
Create the permission.
curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" \ -H 'Content-Type: application/json' \ $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:historyservice \ -d '{"description":"Grants access to the contents of the Components screen"}' curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" \ -H 'Content-Type: application/json' \ $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:system-health \ -d '{"description":"Grants access to the Components screen"}' -
Grant the following privileges to the user
uid.curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:historyservice/users/<uid>/full curl -X PUT --cacert dcos-ca.crt \ -H "Authorization: token=$(dcos config show core.dcos_acs_token)" $(dcos config show core.dcos_url)/acs/api/v1/acls/dcos:adminrouter:ops:system-health/users/<uid>/full
 DC/OS Documentation
DC/OS Documentation